Easily Force Pi-Hole for DNS on a UDM-Pro

Table of Contents
INTRO
A UDM-Pro and Pi-Hole working together is a great combination. In a previous post, here. I went through the process of installing Pi-Hole and configuring it on a router flashed with DD-WRT firmware and explained how to block the circumvention of users trying to use DNS servers other than the Pi-Hole device.
This last summer I migrated away from DD-WRT to an Ubiquiti Unifi setup. In this post I explain how to block the circumvention of Pi-Hole on a Unifi Dream Machine Pro.
LOGIN TO THE UDM-PRO
Now, this post will assume you already have things working and a Pi-Hole device configured and ready to implement into your Unifi system. Refer to my previous post for more context and help. As of writing the firmware on my Dream Machine Pro is at version: 1.12.22 with Network application at: 7.2.92.
Login to the Web portal of your Dream Machine Pro, the default IP is: 192.168.1.1.

CREATE THE DNS GROUP
- Click “Settings” on sidebar on the left when in the Network application.
- Then click “Profiles” on the sidebar that appears on the left.
- Then scroll down to find “Port and IP Groups”
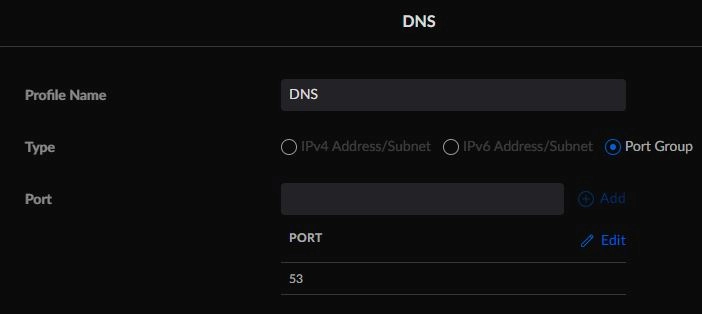
- Create a Port Group called DNS for port 53.
- Then scroll down to find “Port and IP Groups”
- Then click “Profiles” on the sidebar that appears on the left.
CREATE THE FIREWALL RULES
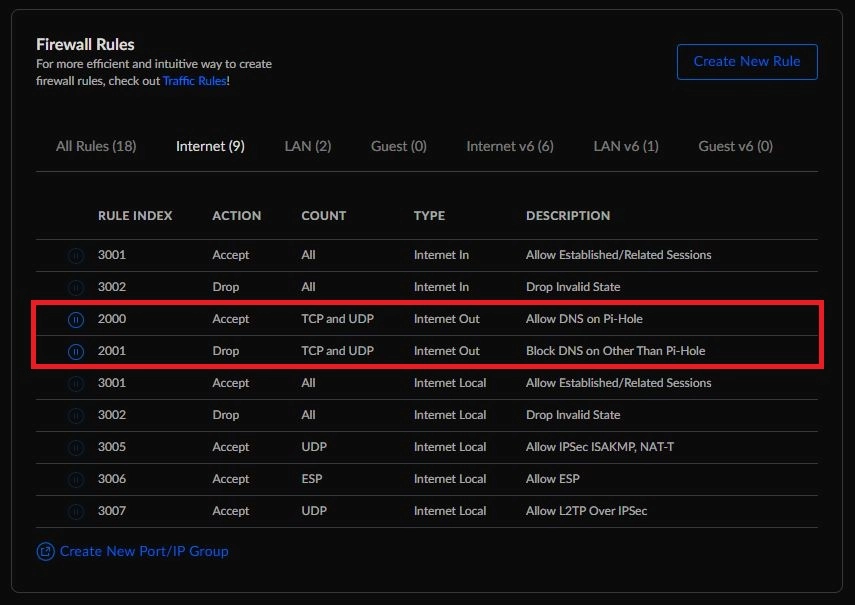
Then back in the Network application, go to, Settings > Firewall and Security and create the following rules as shown below. As you can see, I have created rules 2000 and 2001. Next, I will post my configuration of those rules.
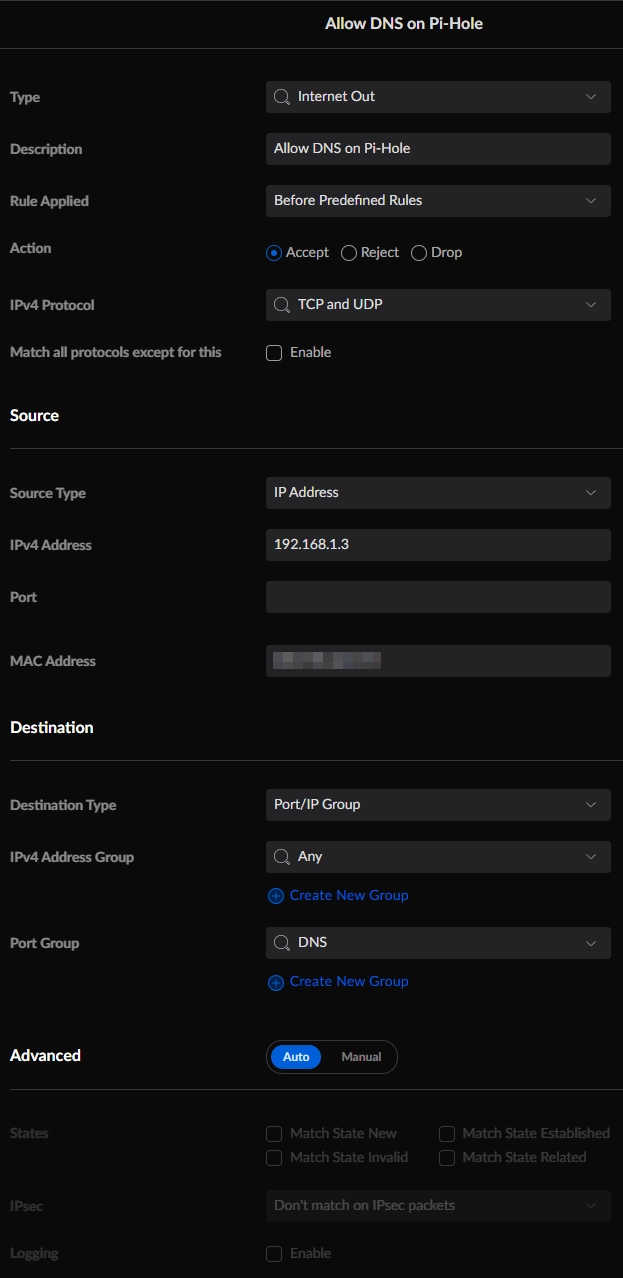
Here is the configuration for rule 2000:
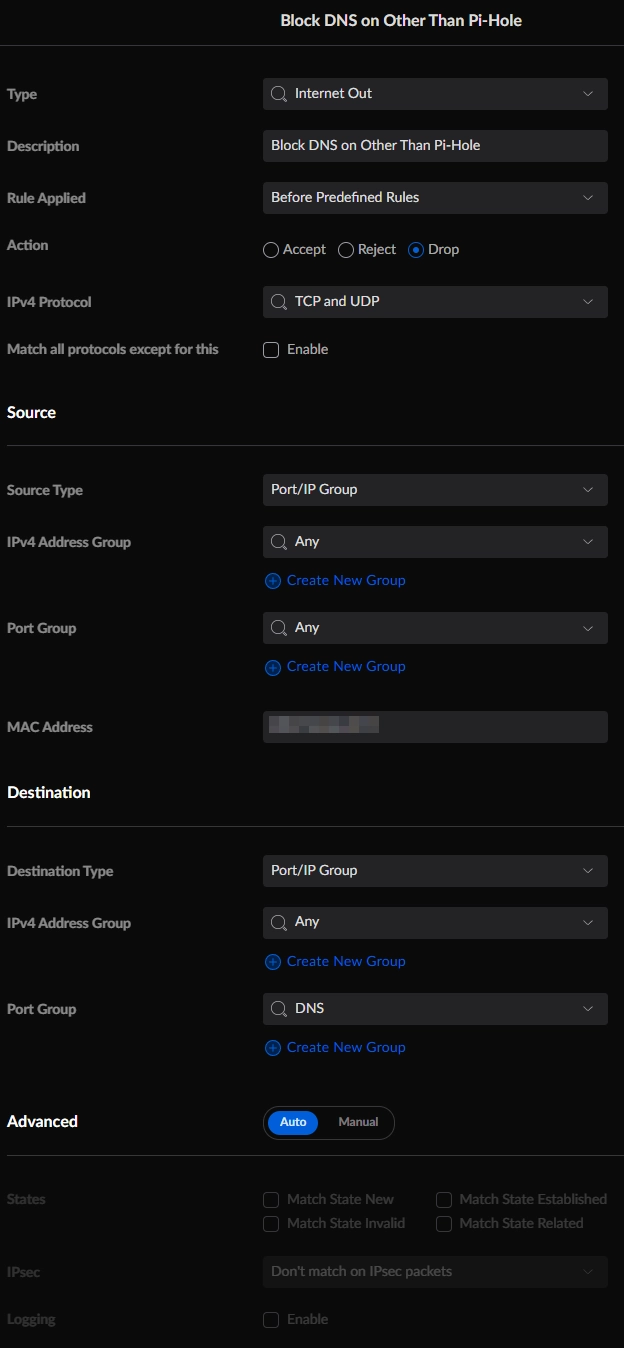
Here is the configuration for rule 2001:
CONFIGURING THE DNS SERVER ON THE DREAM MACHINE PRO
Once done, you will need to have the DHCP Name Server configured to the IP address of your Pi-Hole device on the Dream Machine Pro, and you do this by going to:
- Network application
- Click “Settings” on sidebar on the left.
- Then click “Networks” on the sidebar that appears on the left.
- Then open the “Default” network to view its settings.
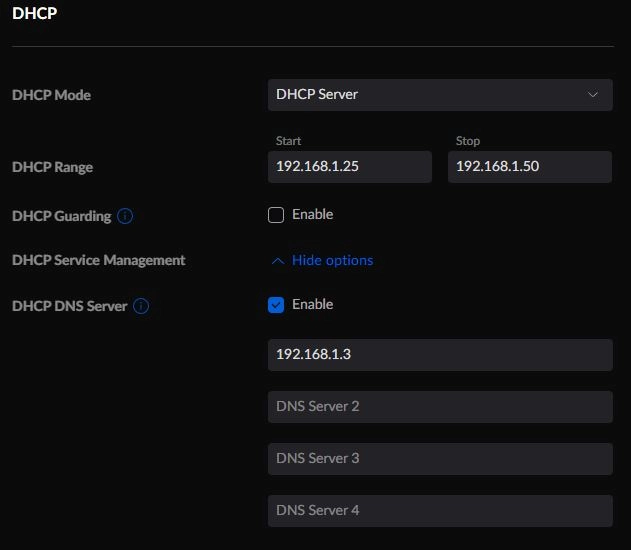
- Scroll down to find “DHCP” then by “DHCP Service Management” area select “Show options”. Input your Pi-Hole device’s IP under DHCP DNS Server.
- Then open the “Default” network to view its settings.
- Then click “Networks” on the sidebar that appears on the left.
- Click “Settings” on sidebar on the left.
REDIRECT DNS REQUESTS TO PI-HOLE OPTION
A better way instead of blocking DNS requests from other servers like Google’s DNS we should instead have the UDM-Pro redirect those requests to Pi-Hole. While I wanted to do this originally, I didn’t have an answer, but now I do. These commands may also work in DD-WRT. I
logged into my UDM-Pro with SSH and ran the following commands:
iptables -t nat -A PREROUTING ! -s 192.168.1.3 -p tcp --dport 53 -j DNAT --to 192.168.1.3
iptables -t nat -A PREROUTING ! -s 192.168.1.3 -p udp --dport 53 -j DNAT --to 192.168.1.3
iptables -t nat -A POSTROUTING -m iprange --src-range 192.168.1.2-192.168.1.254 -j MASQUERADEI used a program called Putty to do this. You will need to enable SSH by going to the area before you select any of the Unifi applications, such as Network, Protect, etc, and then going to Settings -> Advanced -> SSH and enabling the option. Once done you can use Putty to SSH into your UDM-Pro.
- Username: root
- Password: The password you use to login to your UDM-Pro’s web interface.
- I believe this is the default when you enable SSH under, Settings (before any applications) -> System. If not it’s possible the password was changed to something else, but you can change it there. There is also SSH credential settings under Network -> Settings -> System -> Network Device SSH Authentication for directly accessing devices via SSH.
Paste each line one by one. It may take 30 seconds to a minute to see the changes and be sure to clear your DNS cache in Windows with the command ipconfig /flushdns before testing. These added commands will be removed after a reboot.
UDM / UDM-PRO ON-BOOT SCRIPT
You can have a script run at startup with this. I recently ran into a customer that uses primarily Chromebooks and had issues with people watching pornography. I configured them to use CleanBrowsing DNS, but it’s not working because I assume the Chromebooks are using Google DNS. The firewall rules above would prevent them from connecting to the internet.
So, I explained this, and they invited us to have Admin permissions to their Cloud Portal, then I used their VPN configuration to be able to SSH into their UDM-Pro from my office but before I did so I tested on my own equipment, and it works. Here is what I did.
- SSH into the UDM-Pro using Putty.
- Download Putty here.
curl -fsL "https://raw.githubusercontent.com/unifi-utilities/unifios-utilities/HEAD/on-boot-script/remote_install.sh" | /bin/shNext change to the directory where we will place our on-boot script/s.
cd /data/on_boot.dCreate our blank script file.
- If the curser gets stuck use Ctrl + C to get out, type “ls” to get a list of files in the current directory to confirm the blank file was created.
cat > 07-dns-redirection-on-port-53.shWe will now insert the following text into the blank script file with the VI editor.
- You must be in insert mode to edit, press “i” to get in then start adding lines to your script. When using Putty press the right-click key once to paste clipboard data into the terminal.
vi 07-dns-redirection-on-port-53.shOnce done putting in the lines like my example below, use Esc to get out of INSERT mode and then type, “:x”, then hit enter, to exit and save the changes.
#!/bin/sh
## Configure DNS Redirection on Port 53
iptables -t nat -A PREROUTING ! -s 192.168.1.3 -p tcp --dport 53 -j DNAT --to 192.168.1.3
iptables -t nat -A PREROUTING ! -s 192.168.1.3 -p udp --dport 53 -j DNAT --to 192.168.1.3
iptables -t nat -A POSTROUTING -m iprange --src-range 192.168.1.2-192.168.1.254 -j MASQUERADE- IMPORTANT: I discovered that if you include the gateway in the IP range, it breaks the VPNs from connecting. Exclude the gateway to resolve this, in my example I started the range at 192.168.1.2 my gateway is at 192.168.1.1.
Restart the UDM-Pro and test.
TESTING
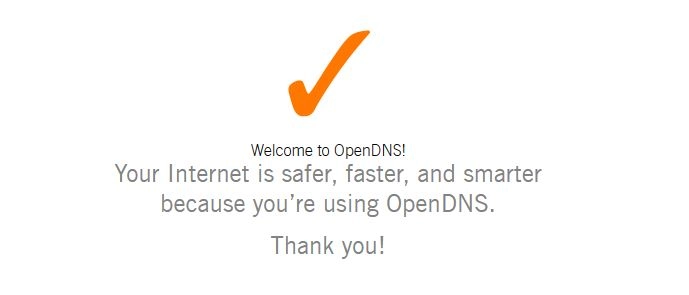
To test the commands, I disabled the firewall rules, 2000 and 2001 I created in this guide and set the network adapter on my computer to use Google’s DNS server at 8.8.8.8 and flushed the DNS cache in Windows with ipconfig /flushdns. Going to the OpenDNS Welcome page confirms that the changes are working.
I am using OpenDNS Family Shield IPs:
- 208.67.222.123
- 208.67.220.123
I like these because the welcome page they have helps with troubleshooting and testing.
Checking the query log in Pi-Hole shows that the DNS requests are getting to it. The downside is that you can’t see which client is querying what when using masquerade, as all client requests show up as from unifi.localdomain.
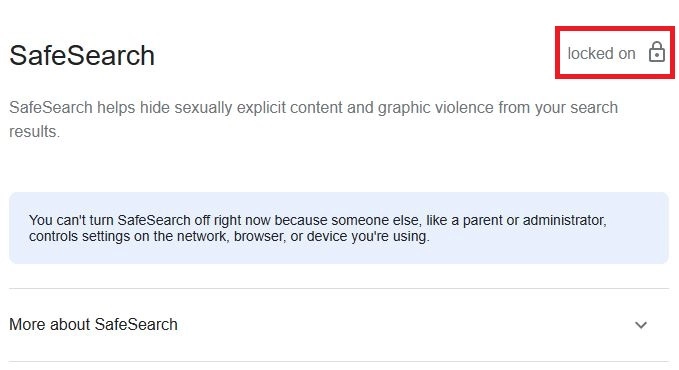
If you have decided to use CleanBrowsing DNS which forces Safe Search or implemented custom DNS changes to your Pi-Hole or other self-hosted DNS server using either Hosts file edits and/or CNAME changes with the values below, then you should test that also.
PI-HOLE DNS RECORDS
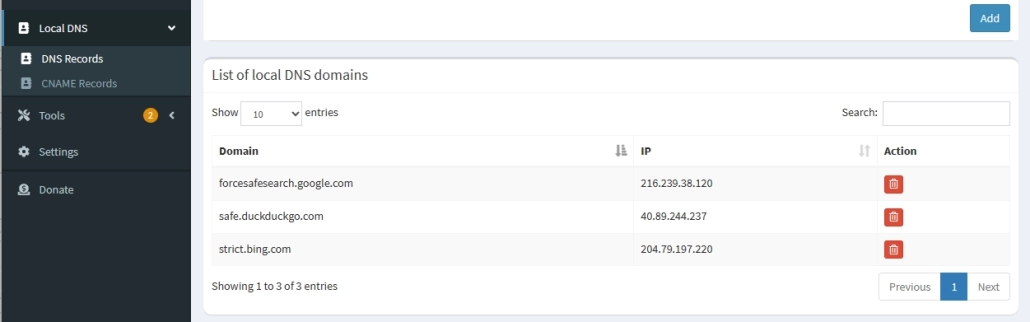
216.239.38.120 restrict.youtube.com
216.239.38.119 restrictmoderate.youtube.com
216.239.38.120 forcesafesearch.google.com
204.79.197.220 strict.bing.com
40.89.244.237 safe.duckduckgo.comPI-HOLE CNAME RECORDS
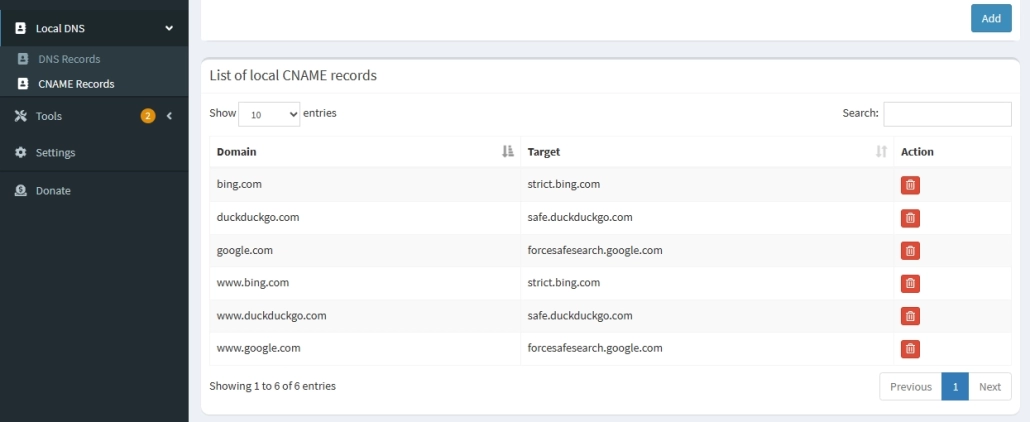
# Google Safe Search
cname=google.com,forcesafesearch.google.com
cname=www.google.com,forcesafesearch.google.com
# Bing Safe Search
cname=bing.com,strict.bing.com
cname=www.bing.com,strict.bing.com
# DuckDuckGo Safe Search
cname=duckduckgo.com,safe.duckduckgo.com
cname=www.duckduckgo.com,safe.duckduckgo.comSAFE-SEARCH FORCE CHECK
You can also restrict YouTube.
# YouTube Restricted
# You can also implement a moderate setting instead. Replace restrict.youtube.com with restrictmoderate.youtube.com
cname=youtube.com,restrictmoderate.youtube.com
cname=www.youtube.com,restrictmoderate.youtube.com
cname=m.youtube.com,restrictmoderate.youtube.com
cname=youtubei.googleapis.com,restrictmoderate.youtube.com
cname=youtube.googleapis.com,restrictmoderate.youtube.com
cname=youtube-nocookie.com,restrictmoderate.youtube.com
cname=www.youtube-nocookie.com,restrictmoderate.youtube.comHopefully a feature will be added in the firmware for this in the future, so we don’t need to use third-party scripts.
LIMITATIONS
DNS has changed in last few years with DNS over TLS (DoT), and DNS over HTTPS (DoH). Windows clients, and browsers like Microsoft Edge and Google Chrome have their own options to enable these:
- Chrome settings -> Privacy and Security -> Security -> Use secure DNS
- Edge settings -> Privacy, search, and services -> Use secure DNS to specify how to lookup the network address for websites
Because of this, Pi-Hole can be circumvented. I tried figuring out a way to work with these features rather than block them but couldn’t figure out a good way. DoT works with port 853 so I could block that port completely. DoH works over port 443 and we can’t block that port. Some people are installing packages on Pi-Hole which act as proxies and then implement firewall rules.
I think the best option is to use a firewall with frequent signature updates implemented for very aggressive blocking where DNS is not relied on completely. You could manage Windows endpoints with browser extensions or Group Policies to help but that won’t stop people on unmanaged devices. It appears firewall signatures may be the easiest way to block things now which usually aren’t free, but for security you’re going to have to pay up.
CONCLUSION
Well, that should be it. Test changing the DNS servers manually on a network adapter on a connected client and see if the changes are working. Should be good fun to annoy your tech-savvy kids in the household. If they start complaining, you know it’s working!
Thanks for reading!
My name is Dex Sandel, author at WinReflection.
I am a Christian, conservative, and truth seeker that is not afraid to be vocal on important or controversial issues, silence leads to death. When a person has that courage the enemy tries to send haters and wolves in sheep’s clothing their way. There are many rewards earned in Heaven for those that refuse to give up. There’s more to life than the worldly status quo and that’s why many are sad and depressed, they’re suffocating! Truth and purpose can bring fresh air into one’s life and that’s my mission.
The best is yet to come, and nothing can stop what’s coming!
John 3:16: For God so loved the world that he gave his one and only Son, that whoever believes in him shall not perish but have eternal life.


This is a great guide for this level of setup. I have been happily using Pi-Hole without the rules you show in this guide for catching the DNS messages that bypass Pi-Hole. I thought I would try changing that. I have two questions:
1) This page is written with the assumption that the user has only one Pi Hole set up. I have two for redundancy in case one drops out for whatever reason. I have tried setting up an IP Group in addition to a Port group and substituting the IP Group for the source in your “Allow DNS on Pi-Hole” rule. Does this make sense to you?
2) More importantly, perhaps this whole page should be updated for the latest versions of UnifiOS and Network since there have been quite a few changes to NAT , Rules, and Firewalls recently. I have been toying around with translating your “REDIRECT DNS REQUESTS TO PI-HOLE OPTION” to the Network->Settings->Routinig->NAT screen rules, which I think translate into your iptables commands and won’t require the on-boot-script option to keep the settings persistent after reboot or update to the UDM Pro. I have been playing with the setting there but I can’t figure out for sure how to implement the two Pi-hole set-up on that screen. Any assistance pointing in the right direction would be welcomed.
Thanks, and God Bless,
Lee
Hey Dex,
Does the script still work under the newly released firmware 4.0.6? Just got a UDM PRO, coming from pfsense and missing out the DNS redirect rules and also port forwarding from my wire guard gateway. Hope to get this done with your article.
Thx Dirk
I personally don’t use it anymore but the other client I installed it on I haven’t heard anything and it’s running the latest. There is also a feature now called DNS Shield and you can assign various providers which override DNS servers assigned on the WAN port.
Do you have any recommendations what to do, if Pi-hole fails? Because Fallback dns servers don’t work, in my case.
Have a backup of the SD-CARD, and a spare Pi on-site. Not sure why your redundant DNS servers would not be working.
Sorry, wrong description. DNS Fallbacks work, but the dream machine often prefers them instead of the Pihole. Thats why I don’t use the fallback DNSs. Ping issues seem not to be the problem. Any idea how the udm chooses between first and secondary DNS? So in my case I have no internet connection, if the Pihole fails. Thanks for the efforts.
May I ask what you’re using Pi-Hole for? I am just curious. I would say that you could simply have another Pi-Hole device, just image the SD-Card to another, boot the device and change its IP, then add that Pi-Hole as your secondary DNS for your LAN.
The secondary is supposed to be used if the the first DNS server goes down. For example in some Windows domain networks, I configure the LAN to have the Windows domain controller be the first DNS server, then the secondary is usually Google (8.8.8.8) or Cloudflare (1.1.1.1). What this does is keep the Windows clients in the domain online when I reboot the domain controller or troubleshooting, otherwise they go offline for users.
Hi Dex,
Thank you so much for your article. It is very well done and extremely helpful to kickstart the process. I have a Unifi Dream Machine Special Edition (UDM-SE). I’d like to send you screenshots of what I did in the UDM-SE GUI to make it work as they are a little different. I also found that I needed to NOT include MAC for the “Block DNS on Other Than Pi-Hole IPv4” rule, otherwise it blocked the Pi-hole. Of course, I’m not certain what MAC you blurred out in your screen shot for the deny rule.
Hi Shannon, thank you so much for the complement! I am delighted that you want to send me some images but it’s not necessary. Part of IT is people figuring things out on their own. There is always going to be updates, GUI changes, and more so this guide is just a template. You’re right about the obscured MAC on the “Block DNS on Other Than Pi-Hole IPv4” rule screenshot, I am not sure what I had in there. It might have been the MAC of the UDM-Pro itself. I believe the reason I added the MACs was to possibly prevent spoofing, a foreign IP or device at the same IP as the Pi-Hole or UDM-Pro.
The hope was that adding MAC details would add another layer of security. I am glad you got things working! In the field I have been setting networks to use the Clean Browsing DNS servers, schools, cafes, bars, and many other businesses. I wonder how many people I irritated blocking adult content. Either way, I add my little touch out there to protect networks, and people from themselves.
Hi WinReflection,
Thanks for your informative post. I have a couple of questions they may need simple answers so excuse my n00bness :)
i) the MAC address you have obscured, what device is that for and is it essential to making the rules work ?
ii) After creating the above rules and following your guide (I stopped at the “REDIRECT DNS REQUESTS TO PI-HOLE OPTION” bit), I still get ads/banners popping up on the popular speedtest site of https://www.speedtest.net/ , not on the initial homepage but on the results page after the tests have run (https://ibb.co/zmTX7F9)
Am I doing anything wrong ?
Cheers
Hey sure, no problem.
1. I just obscured the MAC of my Pi-Hole for privacy reasons, probably didn’t need to do so.
2. Those ads should not be present which means something isn’t working.
If using Pi-Hole you need make sure your ad lists are up-to-date and that you have a lot of them. Use nslookup commands to confirm your DNS server if using Windows. Make sure you aren’t using DoT or DoH for DNS also.
Hi winreflection.com owner, Thanks for the educational content!
Can I use this approach to apply these rules only to one of the VLAN’s as opposed to all of the VLAN’s? I would like to use the Firewall rules using the GUI if I can, to keep it simple.
I found a relatively straightforward way to do this on the current GUI (Unify OS 2.5.11): under the “Firewall and Security” tab, scroll down to “Port Forwarding” and then click “Create New Forwarding Rule.” From there, type in your desired parameters. I only had one device noticeably misbehaving, so my rule is simple: https://imgur.com/usYNLs4
-“Source” is the fixed IP of the offending device (in my case a smart TV). However, presumably you could instead use an entire IP address range (i.e. 192.168.30.1/24) if you wanted to redirect your entire VLAN.
-“Port” and “Destination port” obviously would both be 53
-“Forward IP” is the fixed IP of my Raspberry PI with AdGuard/PiHole
-“Protocol” is both
As someone who does not relish the idea of messing around with CLI (I have no coding knowledge and don’t want to break anything I can’t fix), this was easy for me. It persists throughout updates/reboots, and doesn’t require leaving the Unify GUI. If you have multiple devices or subnets you’d like to include, just make multiple rules.
Thank you for your contribution!
Excellent, thank you. Yes, a range 192.168.3.15-192.168.3.18 works
Hmmm after watching the logs, I disagree. The interface this also affects is WAN In thus any errors would allow DNS traffic INTO your network. I know because the initial setting “ANY” was set and I see a few DNS rejections from outside my LAN. This was a first. The rule blocked an external IP from going to another external IP for DNS.
On the other hand, it did redirect internal DNS traffic to the PiHole (as desired).
My concern and reason why I disabled this rule was the potential of allowing external traffic via DNS ports. Risk is not worth it.
I did this and now my Google Hubs won’t work. I think they require google DNS. any thoughts?
Hi Dave, it could be that Pi-Hole is blocking domains that Google Hubs requires to work. If so, you will need to login to the Web Portal of your Pi-Hole device and whitelist those blocked domains. If you go to the query log when attempting to test, you will see which ones are blocked, you can also research which domains Google Hubs needs to work and manually whitelist those. I have found that certain devices, like a Google Nest for example won’t work if you block DNS queries to Google’s DNS servers. In this case, you will want to try the DNS redirection to Pi-Hole method instead.
Hey thanks for the info. if I have multiple subnets do I need to duplicate the last iptables line for each subnet or will just the one you have work for all subnets? Awesome writeup.
That’s a good question, I would need to test it, but yes, any other subnets would need to be added to the last command or an additional command created for each.