Utilizing Datto RMM User-Defined Custom Fields

Table of Contents
Intro
While Datto RMM already gives us so much information about each endpoint I want to talk about the User-Defined Fields (UDFs) feature because it has made my life much easier. There was some information I wanted on the front-page of each device summary so I didn’t need to go digging through multiple tabs and also so I could export to Microsoft Excel.
The Component Store
The community ComStore has many options already available for you to download and add to your portal’s component library. Simply go through the list and add the ones you want. For example, you can have the device’s TPM status and BitLocker recovery keys shown. You can have Office and Windows Product Keys detected. Activation status, a Windows 11 compatibility check, backup product detection, and much more.
Configuring the UDF Job
Under the Administrator account for your portal, go to:
- Setup -> Account Settings -> User-Defined Fields
This is where you will label the header for the value of data that will be in the field, but this is not where you will configure UDFs. Configuring them will be done under Jobs.
In Jobs, create a new job called, “Managed IT [All] – Custom UDFs – Initial Audit” and for Job targets add the following:
- Default Device Filters (All Sites): All Windows Servers
- Default Device Filters (All Sites): All Windows Desktops
For a schedule set it for, “Once an initial audit has completed”. This means whenever a new device is added the job will run and add the UDFs.
You can also repeat the process with a job called, “Managed IT [All] – Custom UDFs – Schedule” where you can set a time each day that Datto RMM will run the UDF scripts for each device to keep the UDFs updated daily. Here is a screenshot of my configuration.
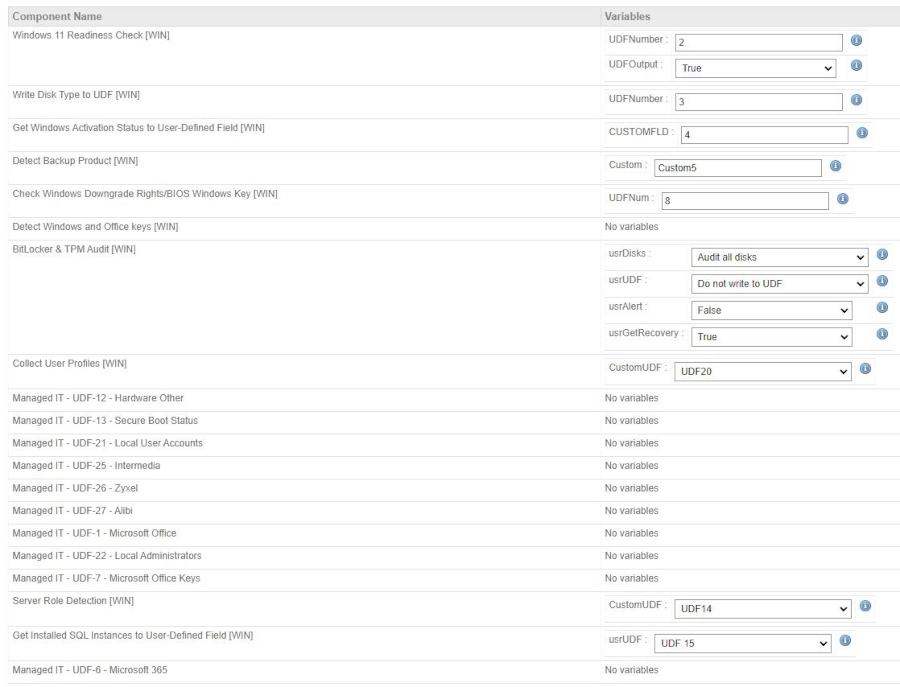
Output Example
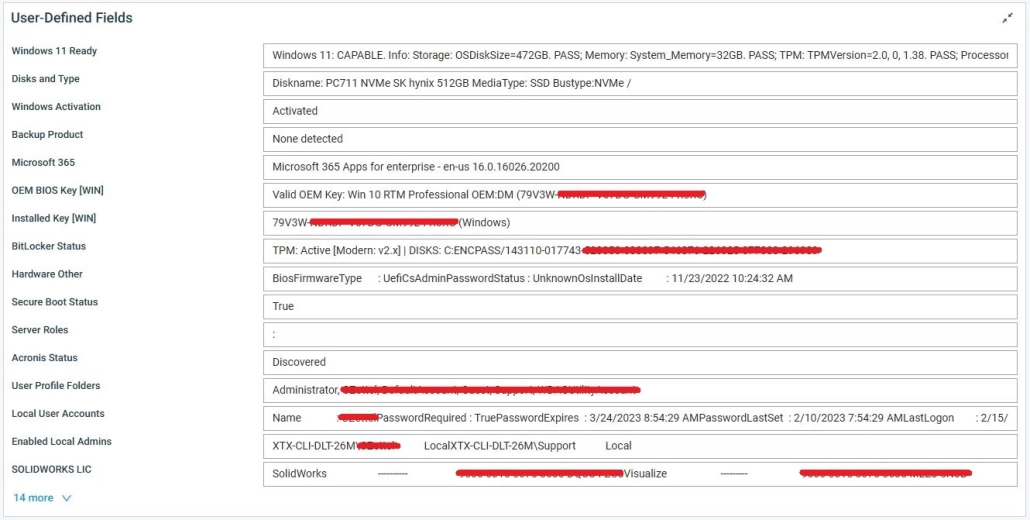
Here is also an example output of the job when it runs on an endpoint in New UI. I removed information that I would rather not share.
As you can see, I can get a lot of information on the summary page of an endpoint. I can tell if an endpoint has an SSD, if it’s using Bitlocker, how it’s activated, if it’s running UEFI and Secure Boot, and more.
I can have the Windows OEM Product Key stored in BIOS given to me as well as the Windows Product Key stored in the Registry and used to activate Windows.
I also have the Bitlocker Recovery Key. User Profile Folders, Local User Accounts, and Enabled Local Administrators at the end. All of these fields get stored into columns as well and can be exported to an Excel document for auditing purposes.
Also, having the information acts as a backup in-case you lose Bitlocker or Product Key information.
PowerShell Script
If you notice from my configuration I have several components that start with Managed IT. You will not find these in the Component Store for download as they are my own custom scripts that I created. The scripts run and then the output is placed in the registry under a certain User-Defined Field (UDF) number of my choosing. This is how we can customize the fields we want when no component is available for it.
Here is my script for querying all Local Administrators:
# Get All Local Administrators
$ErrorActionPreference = 'SilentlyContinue'
# Get All Local Administrators
$Administrators = Get-LocalGroupMember -Group "Administrators" | Select-Object Name | Format-Table -HideTableHeaders
# Output
$AdministratorsList = ($Administrators | Out-String).Trim(); $AdministratorsList
# Validate the UDF Variable
[int]$env:usrUDF = '22'
if ([int]$env:usrUDF -and [int]$env:usrUDF -match '^\d+$') {
# Validate the variable value is between 1 and 30
if ([int]$env:usrUDF -ge 1 -and [int]$env:usrUDF -le 30) {
New-ItemProperty -Path "HKLM:\SOFTWARE\CentraStage" -Name Custom$env:usrUDF -Value $AdministratorsList -Force | Out-Null
Write-Host "Value written to User-Defined Field $env:usrUDF`."
}
else {
Write-Host "User-Defined Field value must be an integer between 1 and 30."
}
} else {
Write-Host "User-Defined Field value invalid or not specified. Not writing results to the User-Defined Field."
}The example is given so you can customize yourself with your own scripts.
Component UDF Scripts
Below are the custom UDF scripts that I used to gather the details above. Simply add to the example script above before the “# Validate the UDF Variable” line and replace the UDF number with the one you desire.
Then on line 12 replace with the correct variable in the script for output.
Managed IT – UDF 1 – Microsoft Office
# Get Microsoft Office Products Installed
$ErrorActionPreference = 'SilentlyContinue'
# Get Microsoft Office Products Installed
$Microsoft32Bit = Get-ItemProperty HKLM:\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\* | where{$_.DisplayName -LIKE 'Microsoft Office P*' -or $_.DisplayName -LIKE 'Microsoft Office H*' -or $_.DisplayName -LIKE 'Microsoft Office S*' -or $_.DisplayName -LIKE 'Microsoft Visio*' -or $_.DisplayName -LIKE 'Microsoft Lync*' -or $_.DisplayName -LIKE 'Microsoft P*' -or $_.DisplayName -LIKE 'Microsoft O*' -or $_.DisplayName -LIKE 'Microsoft Access*' -or $_.DisplayName -LIKE 'Microsoft Excel*' -or $_.DisplayName -LIKE 'Microsoft Word*' -or $_.DisplayName -LIKE 'Microsoft InfoPath*'} | Select-Object DisplayName, DisplayVersion | Format-Table -HideTableHeaders
$Microsoft64Bit = Get-ItemProperty HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\* | where{$_.DisplayName -LIKE 'Microsoft Office P*' -or $_.DisplayName -LIKE 'Microsoft Office H*' -or $_.DisplayName -LIKE 'Microsoft Office S*' -or $_.DisplayName -LIKE 'Microsoft Visio*' -or $_.DisplayName -LIKE 'Microsoft Lync*' -or $_.DisplayName -LIKE 'Microsoft P*' -or $_.DisplayName -LIKE 'Microsoft O*' -or $_.DisplayName -LIKE 'Microsoft Access*' -or $_.DisplayName -LIKE 'Microsoft Excel*' -or $_.DisplayName -LIKE 'Microsoft Word*' -or $_.DisplayName -LIKE 'Microsoft InfoPath*'} | Select-Object DisplayName, DisplayVersion | Format-Table -HideTableHeaders
# Merge Values and Output
$Microsoft = ($Microsoft32Bit, $Microsoft64Bit | Out-String).Trim(); $MicrosoftManaged IT – UDF 6 – Microsoft 365
# Get Microsoft Office 365 Products Installed
$ErrorActionPreference = 'SilentlyContinue'
# Get Microsoft Office 365 Products Installed
$Microsoft32Bit = Get-ItemProperty HKLM:\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\* | where{$_.DisplayName -like 'Microsoft 365*'} | Select-Object DisplayName, DisplayVersion | Format-Table -HideTableHeaders
$Microsoft64Bit = Get-ItemProperty HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\* | where{$_.DisplayName -like 'Microsoft 365*'} | Select-Object DisplayName, DisplayVersion | Format-Table -HideTableHeaders
# Merge Values and Output
$Microsoft365 = ($Microsoft32Bit, $Microsoft64Bit | Out-String).Trim(); $Microsoft365Managed IT – UDF 7 – Microsoft Office Keys
# Get Microsoft Office Product Keys:
$ErrorActionPreference = 'SilentlyContinue'
function Search-RegistryKeyValues {
param(
[string]$Path,
[string]$valueName
)
Get-ChildItem $Path -recurse -ea SilentlyContinue |
% {
if ((Get-ItemProperty -Path $_.PsPath -ea SilentlyContinue) -match $valueName)
{
$_.PsPath
}
}
}
# Find registry key that has value: "digitalproductid"
# 32-Bit Versions:
$Key = Search-RegistryKeyValues "HKLM:\SOFTWARE\Microsoft\Office" "digitalproductid"
if ($Key -eq $null) {
# 64-Bit Versions:
$Key = Search-RegistryKeyValues "HKLM:\SOFTWARE\WOW6432Node\Microsoft\Office" "digitalproductid"
if ($Key -eq $null) {Write-Host "Microsoft Office is NOT Installed.";break}
}
$ValueData = (Get-ItemProperty $Key).digitalproductid[52..66]
# Decrypt Base24 Encoded Binary Data:
$ProductKey = ""
$Chars = "BCDFGHJKMPQRTVWXY2346789"
for ($i = 24; $i -ge 0; $i--) {
$r = 0
for ($j = 14; $j -ge 0; $j--) {
$r = ($r * 256) -bxor $ValueData[$j]
$ValueData[$j] = [math]::Truncate($r / 24)
$r = $r % 24
}
$ProductKey = $Chars[$r] + $ProductKey
if (($i % 5) -eq 0 -and $i -ne 0) {
$ProductKey = "-" + $ProductKey
}
}
$MSOfficeKey = ($ProductKey | Out-String).Trim(); $MSOfficeKeyManaged IT – UDF 12 – BIOS Firmware Type
# Get BIOS Firmware Type
$ErrorActionPreference = 'SilentlyContinue'
(Get-ComputerInfo -Property BiosFirmwareType | Format-Table -HideTableHeaders | Out-String).Trim().ToUpper()Managed IT – UDF 13 – Secure Boot Status
# Get Secure Boot Status
$ErrorActionPreference = 'SilentlyContinue'
(Confirm-SecureBootUEFI | Out-String).Trim()Managed IT – UDF 21 – Enabled Local User Accounts
# Get Enabled Local Users
$ErrorActionPreference = 'SilentlyContinue'
(Get-LocalUser | where{$_.Enabled -eq 'True'} | Select-Object Name | Format-Table -HideTableHeaders | Out-String).Trim()Managed IT – UDF 22 – All Local Administrators
# Get All Local Administrators
$ErrorActionPreference = 'SilentlyContinue'
(Get-LocalGroupMember Administrators | Select-Object Name, PrincipalSource | Format-Table -HideTableHeaders | Out-String).Trim()Managed IT – UDF 23 – Enabled Local Administrators
# Get Enabled Local Administrators
$ErrorActionPreference = 'SilentlyContinue'
(Get-LocalGroupMember Administrators | where{(Get-LocalUser $_.SID -EA 0).Enabled} | Select-Object Name | Format-Table -HideTableHeaders | Out-String).Trim()Managed IT – UDF 25 – Intermedia
# Get Intermedia Products Installed
$ErrorActionPreference = 'SilentlyContinue'
# Get Intermedia Products Installed
$Intermedia32Bit = Get-ItemProperty HKLM:\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\* | where{$_.Publisher -like 'Intermedia*'} | Select-Object DisplayName, DisplayVersion | Format-Table -HideTableHeaders
$Intermedia64Bit = Get-ItemProperty HKLM:\Software\Microsoft\Windows\CurrentVersion\Uninstall\* | where{$_.Publisher -like 'Intermedia*'} | Select-Object DisplayName, DisplayVersion | Format-Table -HideTableHeaders
# Merge Values and Output
$Intermedia = ($Intermedia32Bit, $Intermedia64Bit | Out-String).Trim(); $IntermediaManaged IT – UDF 26 – Zyxel
# Get Zyxel Products Installed
$ErrorActionPreference = 'SilentlyContinue'
# Get Zyxel Products Installed
$Zyxel32Bit = Get-ItemProperty HKLM:\Software\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\* | where{$_.Publisher -like 'Zyxel*'} | Select-Object DisplayName, DisplayVersion | Format-Table -HideTableHeaders
$Zyxel64Bit = Get-ItemProperty HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\* | where{$_.Publisher -like 'Zyxel*'} | Select-Object DisplayName, DisplayVersion | Format-Table -HideTableHeaders
# Merge Values and Output
$Zyxel = ($Zyxel32Bit, $Zyxel64Bit | Out-String).Trim(); $ZyxelManaged IT – UDF 27 – Alibi
# Get Alibi Products Installed
$ErrorActionPreference = 'SilentlyContinue'
# Get Alibi Products Installed
$Alibi32Bit = Get-ItemProperty HKLM:\Software\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\* | where{$_.Publisher -like 'Observint Technologies*'} | Select-Object DisplayName, DisplayVersion | Format-Table -HideTableHeaders
$Alibi64Bit = Get-ItemProperty HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\* | where{$_.Publisher -like 'Observint Technologies*'} | Select-Object DisplayName, DisplayVersion | Format-Table -HideTableHeaders
# Merge Values and Output
$Alibi = ($Alibi32Bit, $Alibi64Bit | Out-String).Trim(); $AlibiManaged IT – UDF 28 – Solidworks Serials
# Get Solidworks Serial Numbers
$ErrorActionPreference = 'SilentlyContinue'
# Get Solidworks Serial Numbers
$SolidworksMain = Get-ItemProperty -Path "HKLM:\SOFTWARE\SolidWorks\Licenses\Serial Numbers" -Name "SolidWorks" | Select-Object Solidworks | Format-Table
$SolidworksVisualize = Get-ItemProperty -Path "HKLM:\SOFTWARE\SolidWorks\Licenses\Serial Numbers" -Name "Visualize" | Select-Object Visualize | Format-Table
# Merge Values and Output
$SolidworksSerials = ($SolidworksMain, $SolidworksVisualize | Out-String).Trim(); $SolidworksSerialsConclusion
Hopefully this can save you some time in auditing. Make sure you create a second duplicate job called, “Managed IT [All] – Custom UDFs – Schedule” other than the initial audit job and set that job to run every day at around 11:00 AM. I find most computers are on around 11:00 AM, this way the information stays updated after the initial audit.
My name is Dex Sandel, author at WinReflection.
I am a Christian, conservative, and truth seeker that is not afraid to be vocal on important or controversial issues, silence leads to death. When a person has that courage the enemy tries to send haters and wolves in sheep’s clothing their way. There are many rewards earned in Heaven for those that refuse to give up. There’s more to life than the worldly status quo and that’s why many are sad and depressed, they’re suffocating! Truth and purpose can bring fresh air into one’s life and that’s my mission.
The best is yet to come, and nothing can stop what’s coming!
John 3:16: For God so loved the world that he gave his one and only Son, that whoever believes in him shall not perish but have eternal life.


Hi,
I found the article really useful. Thanks for placing it.
Is there any way to read the value of a User defined field and based on it modify another User defined field?
example: I have the purchase date of laptops and desktops in a User defined field. I created another field named “Marked for replacement”.
I want to use this purchase date to calculate if device needs to be replaced already or not, and if that’s the case modify the field “Marked for replacement”. Life could be different for laptops, let’s say 3 years, while for desktops it can be 4 years. Therefore I also need to check the “Device Type” field to do the calculation.
I think it can be done, but I didn’t find the way to obtain the data from those user defined fields from an script.
Can you help me or provide me some guidance?
Thanks a lot!
Hi Carles, I am glad you found the post helpful and thanks for letting me know!
The UDFs are just values placed in the registry and then Datto RMM, whenever it audits the device it looks at those values and places them into the Device Summary area. You would need to create a PowerShell script to make the edits you’re looking to have done, and maybe run a schedule. I think what you’re doing can be done and I would recommend using ChatGPT for help.
I would simply ask ChatGPT to give you a template to read a device’s purchase date value from the registry UDF key location and then have logic to determine the age of the device and if said age meets criteria then edit the “Mark for replacement” UDF key in the registry.
Datto RMM will then see that value on the device’s next audit and should be visible to you.